Citrix ADC (formerly NetSceler) is, without doubt, one of the top enterprise Application Delivery Controllers on the market and the preferred solution for many organizations. It is offered in many different form factors, from physical to virtual appliances and even containers.
Citrix ADC is also available on Azure, which makes it ideal not only for experimenting and getting to know it better but also for using it to publish applications and services.
I've created a bicep template to serve as a starting point so that you can easily create an instance and get to know the resources required. The main template creates a subscription-level deployment that separates the resources into different resource groups.
The resources to be deployed include:
- virtual network
- network security group
- network card
- public IP
- virtual machine
Going through the bicep files, we have a main template file (
main.bicep) that uses two separate modules to deploy the vNet (
vnet.bicep) and the ADC (
adc.bicep) respectively. All the ADC-related resources - such as the NIC, NSG, etc. - are part of the ADC module. If you already have a vNet, you can just deploy the adc bicep file using just the id of the subnet to connect to.
To make the process easier, I've also created a script that creates the deployment via Azure CLI. Just make sure you're logged in and using the right subscription.
The ADC is deployed with a public IP address so that you can reach it over the internet. The rules on the NSG allow HTTPS and SSH traffic so as soon the deployment completes, update them with your source IPs to increase security!
The bicep files are available on my Github account over here. To deploy, use the Deploy to Azure button below or download a copy of the files and submit the deployment using Azure CLI.

The first step of the deployment process using the above button is to provide values for the deployment. From that point on, the only thing left to do is to create the deployment:
When the deployment is completed, two resource groups should have been created. The networking one that will contain the vNet:
and the ADC resource group:
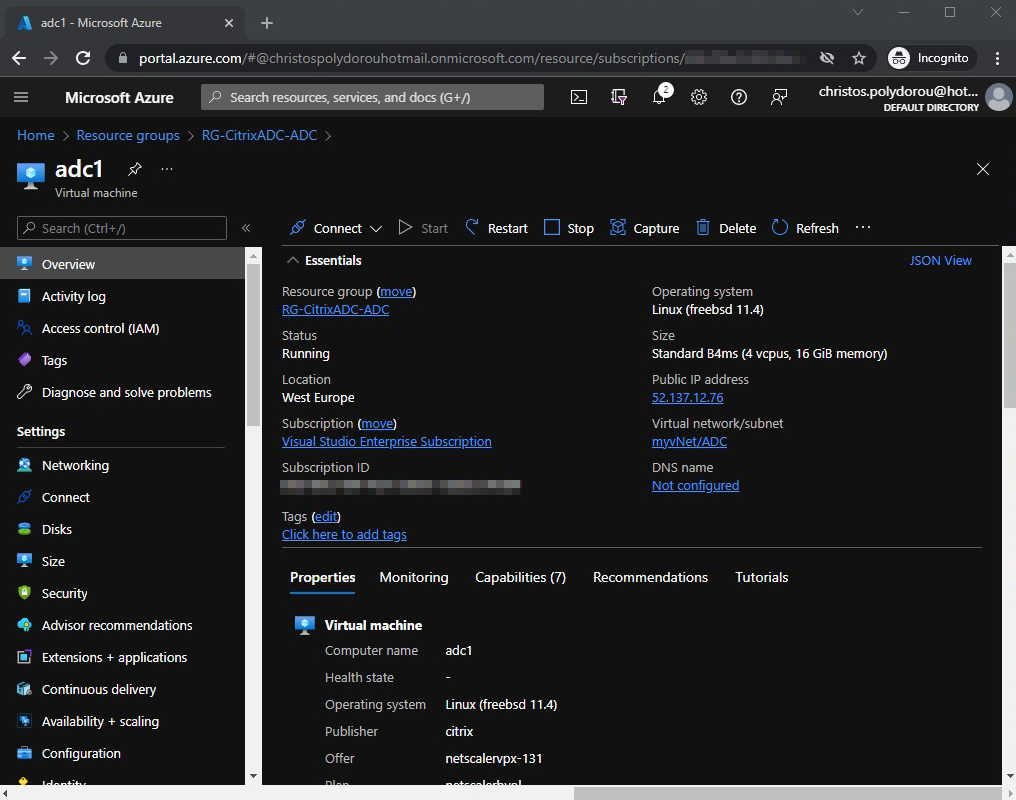
If we open the adc virtual machine, we can see that the public IP that has been assigned to it on the right:
You can login to the management interface of the ADC using a browser and its public IP. There will be a security warning since the appliance will be using self-signed certificates, but you should block internet access anyway:
You can now proceed with the configuration on the appliance!