NetScaler InSight Center Authentication Delegation
Whenever I'm called to setup or troubleshoot Citrix NetScaler performance issues, I try to bring Citrix InSight Center into the game.
InSight Center is a Linux based Virtual Machine which gathers AppFlow performance data from the NetScaler thus helping with performance troubleshooting.
I am not a fan of local user accounts on any system for many reasons, so I'll show you how to delegate the user authentication of the InSight Center to Active Directory.
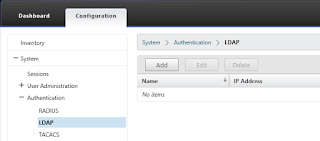
Let's start with logging on to the InSight Center using the default administrator account "nsroot" and navigating to the "Authentication" node under "System". Here we see all the available authentication methods supported: RADIUS, LDAP and TACACS. Since we want to delegate the authentication to Active Directory, we're interested in LDAP.
Select the "LDAP" methods, and then click "Add" to add a server. Fill in the IP address of a domain controller (or a Load Balancing VIP), the usual port of LDAP 389 and "AD" as the Type. If you're using secure LDAP, you may have trouble with the certificates so the option "Validate LDAP Certificate" may help you out. If you are going to add the users to the groups directly, you do not have to use the nested group option. You may also use filters on the LDAP connection to narrow down the results and exclude some users.
Under "Connection Settings" fill the "Base DN" which is the OU that contains the users (includes the child OUs) in LDAP format like "DC=lab, DC=local", the DN of an administrator user and his password. I recommend using an account dedicated to this purpose.
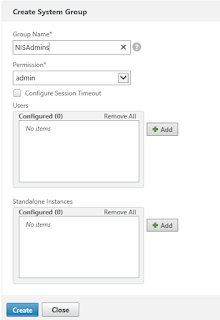
Now that we have configured the LDAP server and the connection details, we have to create the groups and their roles. I usually create at least two Active Directory groups for InSight Center, NISAdmins and NISReadOnly. Whatever groups you have on Active Directory, take a note of the names as you have to use the exact same names when you create the groups on the InSight Center. Navigate to the "User Administration" menu under "System", click on "Groups" and then "Add" to add a group. When creating each group, assign the relevant permission level.
Finally, you have to set the authentication type, navigate to the authentication options under "System" and click on "Authentication Configuration". Select "LDAP" as the server type and your server as "Server Name". I suggest you enable the fallback on local authentication in order to be able to login in case there's something wrong with Active Directory or the network.
In case you're facing problems with external authentication, you can use the aaad.debug file, those of you familiar with the NetScaler will surely know it, saved at /tmp. Log in using console or SSH and change to the /tmp directory. Use cat to show the contents of the file and try to login using the external authentication user.
InSight Center is a Linux based Virtual Machine which gathers AppFlow performance data from the NetScaler thus helping with performance troubleshooting.
I am not a fan of local user accounts on any system for many reasons, so I'll show you how to delegate the user authentication of the InSight Center to Active Directory.
Let's start with logging on to the InSight Center using the default administrator account "nsroot" and navigating to the "Authentication" node under "System". Here we see all the available authentication methods supported: RADIUS, LDAP and TACACS. Since we want to delegate the authentication to Active Directory, we're interested in LDAP.
Select the "LDAP" methods, and then click "Add" to add a server. Fill in the IP address of a domain controller (or a Load Balancing VIP), the usual port of LDAP 389 and "AD" as the Type. If you're using secure LDAP, you may have trouble with the certificates so the option "Validate LDAP Certificate" may help you out. If you are going to add the users to the groups directly, you do not have to use the nested group option. You may also use filters on the LDAP connection to narrow down the results and exclude some users.
Under "Connection Settings" fill the "Base DN" which is the OU that contains the users (includes the child OUs) in LDAP format like "DC=lab, DC=local", the DN of an administrator user and his password. I recommend using an account dedicated to this purpose.
Now that we have configured the LDAP server and the connection details, we have to create the groups and their roles. I usually create at least two Active Directory groups for InSight Center, NISAdmins and NISReadOnly. Whatever groups you have on Active Directory, take a note of the names as you have to use the exact same names when you create the groups on the InSight Center. Navigate to the "User Administration" menu under "System", click on "Groups" and then "Add" to add a group. When creating each group, assign the relevant permission level.
Finally, you have to set the authentication type, navigate to the authentication options under "System" and click on "Authentication Configuration". Select "LDAP" as the server type and your server as "Server Name". I suggest you enable the fallback on local authentication in order to be able to login in case there's something wrong with Active Directory or the network.
In case you're facing problems with external authentication, you can use the aaad.debug file, those of you familiar with the NetScaler will surely know it, saved at /tmp. Log in using console or SSH and change to the /tmp directory. Use cat to show the contents of the file and try to login using the external authentication user.