Generating Alerts On OMS
On the previous articles about Microsoft OMS, we've configured event and log collection from various systems and we've queried the workspace for information. We have the information, wouldn't it be great if we could also act on it?
The Operations Management Suite has a feature named "Alerts" that provides this functionality. Creating alerts is a straight forward and only takes a few minutes. To illustrate the process, we are going to configure an alert for a Windows Server Failover Cluster that hosts the File Server role.
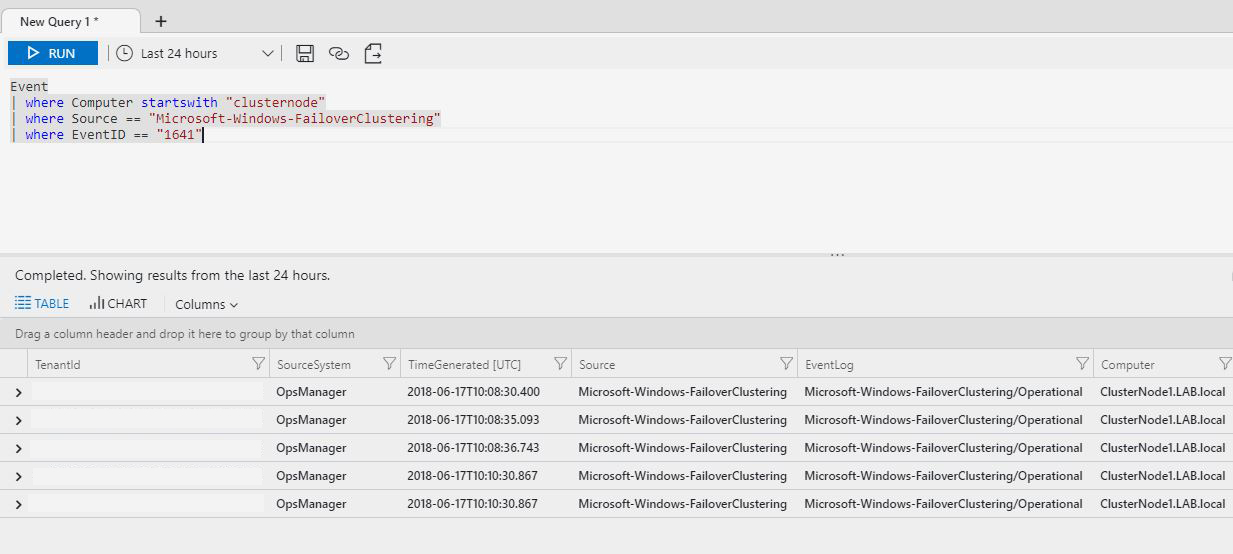
When a cluster resource is moving to another node of the cluster, an event with id 1641 is generated under the source "FaileoverClustering" of the log "Microsoft-Windows-FailoverClustering/Operational".
To create the alert, we are going to need a query that returns the above events:
Let's create the alert. From the main OMS blade, select "Alerts" and then "Create New Rule":
This will bring you to the new alert rule page:
On the first step, we have to select the target OMS workspace and the alert criteria. The current workspace is already selected so the only thing left is to configure the criteria.
The list of available signals is really long. we are going to use the first option though, the "Custom Log Search".
Fill in the query and the threshold and click "Done". Depending how significant the event is, you may update the period and the frequency of the checks.
That was the first step. Now we have to configure the details of the alert:
Moving on to the third and last step, we have to define the action to take:
You can define multiple actions to take when the criteria is met, like sending an email or SMS message, trigger an Azure Function or Webhook and even create a ticket on your service management tools:
When done with the actions, hit the "Create alert rule" button to create the alert. That's it, the rule has been created. Let's test it! I've failed a role to another node and I got the below message:
That's pretty much it!
Related articles
Introduction to Azure Advanced Analytics
Configuring Log and Performance Counter collection on the OMS Workspace
Install and Configure the OMS Windows Agent
Verify the Agent Connectivity to OMS Workspace
Deploying the OMS Windows Agent using DSC
Querying OMS for Performance Data
Querying OMS for Events
Collecting IIS Log Files
Install and Configure the OMS Linux Agent
Syslog Message Collection for OMS from sources that do not support the agent
Generating Alerts from OMS
Update Management using OMS
Monitoring Active Directory Health using OMS
Assessing Security using OMS
Monitoring Microsoft SQL using OMS
Monitoring Azure Activity Log using OMS
The Operations Management Suite has a feature named "Alerts" that provides this functionality. Creating alerts is a straight forward and only takes a few minutes. To illustrate the process, we are going to configure an alert for a Windows Server Failover Cluster that hosts the File Server role.
When a cluster resource is moving to another node of the cluster, an event with id 1641 is generated under the source "FaileoverClustering" of the log "Microsoft-Windows-FailoverClustering/Operational".
To create the alert, we are going to need a query that returns the above events:
Let's create the alert. From the main OMS blade, select "Alerts" and then "Create New Rule":
This will bring you to the new alert rule page:
On the first step, we have to select the target OMS workspace and the alert criteria. The current workspace is already selected so the only thing left is to configure the criteria.
The list of available signals is really long. we are going to use the first option though, the "Custom Log Search".
Fill in the query and the threshold and click "Done". Depending how significant the event is, you may update the period and the frequency of the checks.
That was the first step. Now we have to configure the details of the alert:
Moving on to the third and last step, we have to define the action to take:
You can define multiple actions to take when the criteria is met, like sending an email or SMS message, trigger an Azure Function or Webhook and even create a ticket on your service management tools:
When done with the actions, hit the "Create alert rule" button to create the alert. That's it, the rule has been created. Let's test it! I've failed a role to another node and I got the below message:
That's pretty much it!
Related articles
Introduction to Azure Advanced Analytics
Configuring Log and Performance Counter collection on the OMS Workspace
Install and Configure the OMS Windows Agent
Verify the Agent Connectivity to OMS Workspace
Deploying the OMS Windows Agent using DSC
Querying OMS for Performance Data
Querying OMS for Events
Collecting IIS Log Files
Install and Configure the OMS Linux Agent
Syslog Message Collection for OMS from sources that do not support the agent
Generating Alerts from OMS
Update Management using OMS
Monitoring Active Directory Health using OMS
Assessing Security using OMS
Monitoring Microsoft SQL using OMS
Monitoring Azure Activity Log using OMS